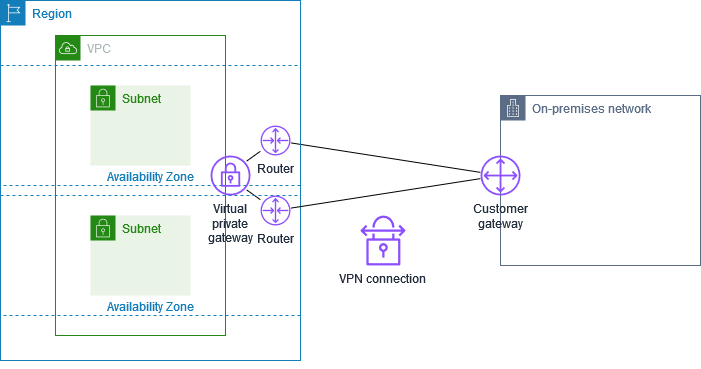
AWS Direct Connect links your internal network to an AWS Direct Connect location over a standard Ethernet fiber-optic cable. One end of the cable is connected to your router, the other to an AWS Direct Connect router.
With this connection, you can create a public virtual interface directly to public AWS services (for example, to Amazon S3) and/or a private virtual interface to your Amazon VPC, bypassing internet service providers in your network path.
An AWS Direct Connect location provides access to AWS in the Region with which it is associated. You can use a single connection in a public Region or AWS GovCloud (US) to access public AWS services in all other public Regions.
The following diagram shows how AWS Direct Connect interfaces with your network.

Features
- AWS Direct Connect supports both the IPv4 and IPv6 communication protocols. IPv6 addresses provided by public AWS services are accessible through AWS Direct Connect public virtual interfaces.
- AWS Direct Connect supports an Ethernet frame size of 1522 or 9023 bytes (14 bytes Ethernet header + 4 bytes VLAN tag + bytes for the IP datagram + 4 bytes FCS) at the link layer. You can set the MTU of your private virtual interfaces.
Network Requirements
Your network must meet the following conditions:
- Your network must use single-mode fiber with a 1000BASE-LX (1310 nm) transceiver for 1 gigabit Ethernet or a 10GBASE-LR (1310 nm) transceiver for 10 gigabit Ethernet.
- Auto-negotiation for the port must be disabled. Port speed and full-duplex mode must be configured manually.
- 802.1Q VLAN encapsulation must be supported across the entire connection, including intermediate devices.
- Your device must support Border Gateway Protocol (BGP) and BGP MD5 authentication.
- (Optional) You can configure Bidirectional Forwarding Detection (BFD) on your network. Asynchronous BFD is automatically enabled for AWS Direct Connect virtual interfaces, but does not take effect until you configure it on your router.
Pricing
AWS Direct Connect has two billing elements:
- port hours and
- outbound data transfer.
Port hour pricing is determined by capacity and connection type (dedicated connection or hosted connection).
Data Transfer Out charges for private interfaces and transit virtual interfaces are allocated to the AWS account responsible for the Data Transfer. There are no additional charges to use a multi-account AWS Direct Connect gateway.
When connecting to AWS services in a different region than which the DX is installed in, any data transfer out of that region is billed at the remote Region data transfer rate.
Direct Connect Gateway
Use AWS Direct Connect gateway to connect your VPCs. You associate an AWS Direct Connect gateway with either of the following gateways:
- A transit gateway when you have multiple VPCs in the same Region
- A virtual private gateway
A Direct Connect gateway is a globally available resource. You can create the Direct Connect gateway in any Region and access it from all other Regions.
Virtual Private Gateways
Each VPC has a virtual private gateway that connects to the Direct Connect gateway using a virtual private gateway association. The Direct Connect gateway uses a private virtual interface for the connection to the AWS Direct Connect location. There is an AWS Direct Connect connection from the location to the customer data center.
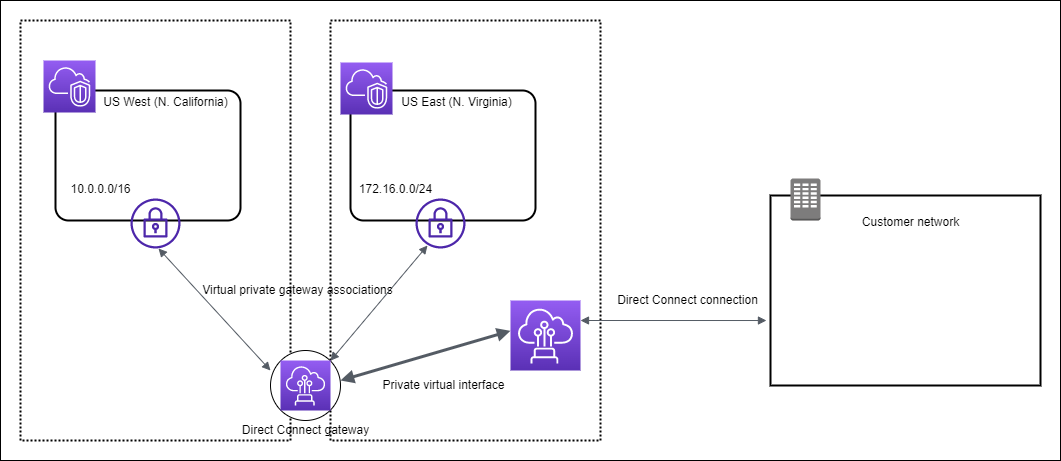
Sharing DX Gateway across accounts
Consider this scenario of a Direct Connect gateway owner (Account Z) who owns the Direct Connect gateway. Account A and Account B want to use the Direct Connect gateway. Account A and Account B each send an association proposal to Account Z. Account Z accepts the association proposals and can optionally update the prefixes that are allowed from Account A’s virtual private gateway or Account B’s virtual private gateway. After Account Z accepts the proposals, Account A and Account B can route traffic from their virtual private gateway to the Direct Connect gateway. Account Z also owns the routing to the customers because Account Z owns the gateway.

But a better way is to use a Transit Gateway.
Transit gateways
The following diagram illustrates how the Transit gateway enables you to create a single connection to your Direct Connect connection that all of your VPCs can use.
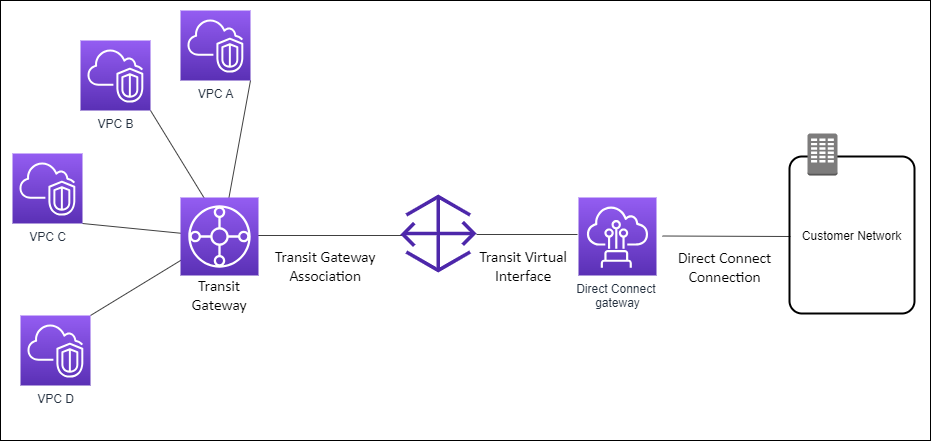
The solution involves the following components:
- A transit gateway that has VPC attachments.
- A Direct Connect gateway.
- An association between the Direct Connect gateway and the transit gateway.
- A transit virtual interface that is attached to the Direct Connect gateway.
This configuration offers the following benefits. You can:
- Manage a single connection for multiple VPCs or VPNs that are in the same Region.
- Advertise prefixes from on-premises to AWS and from AWS to on-premises.
Create a transit gateway attachment to a VPN
- On the navigation pane, choose Transit Gateway Attachments and Choose Create Transit Gateway Attachment.
- For Transit Gateway ID, choose the transit gateway for the attachment.
- For Attachment type, choose VPN.
- For Customer Gateway, do one of the following:
- To use an existing customer gateway, choose Existing, and then select the gateway to use.
If your customer gateway is behind a network address translation (NAT) device that’s enabled for NAT traversal (NAT-T), use the public IP address of your NAT device, and adjust your firewall rules to unblock UDP port 4500.
- To create a customer gateway, choose New, then for IP Address, type a static public IP address and BGP ASN.
For Routing options, choose whether to use Dynamic or Static.
- To use an existing customer gateway, choose Existing, and then select the gateway to use.
- For Tunnel Options, you and set Dead Peer Detect Timeout, supported Internet Key Exchange versions, IP4 CIDR block ranges inside the tunnel, Diffie Hellman group numbers, etc
- Choose Create attachment.